Azure Configurations
Navigate to the Function App named duediligenceapp.
duediligenceapp is the default name that is delivered from the product. Navigate to the respective app as per the current deployment that you have made.
Functions
Configurations
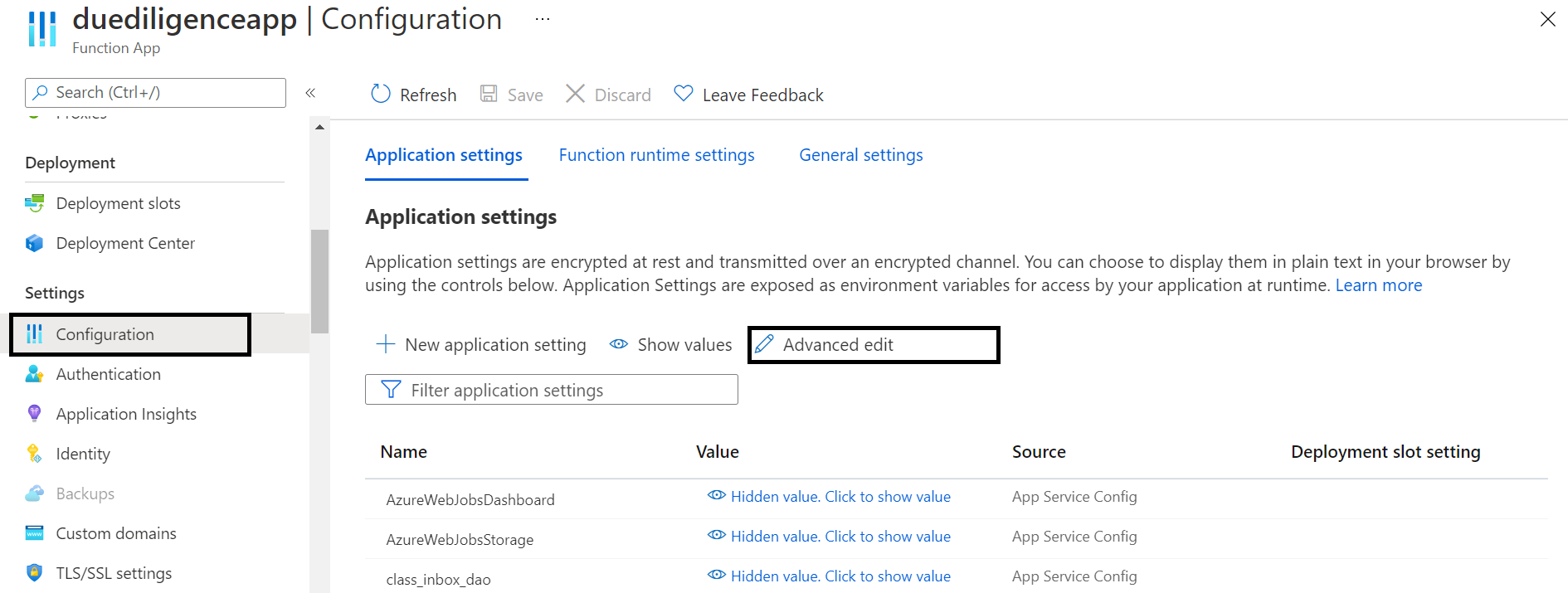
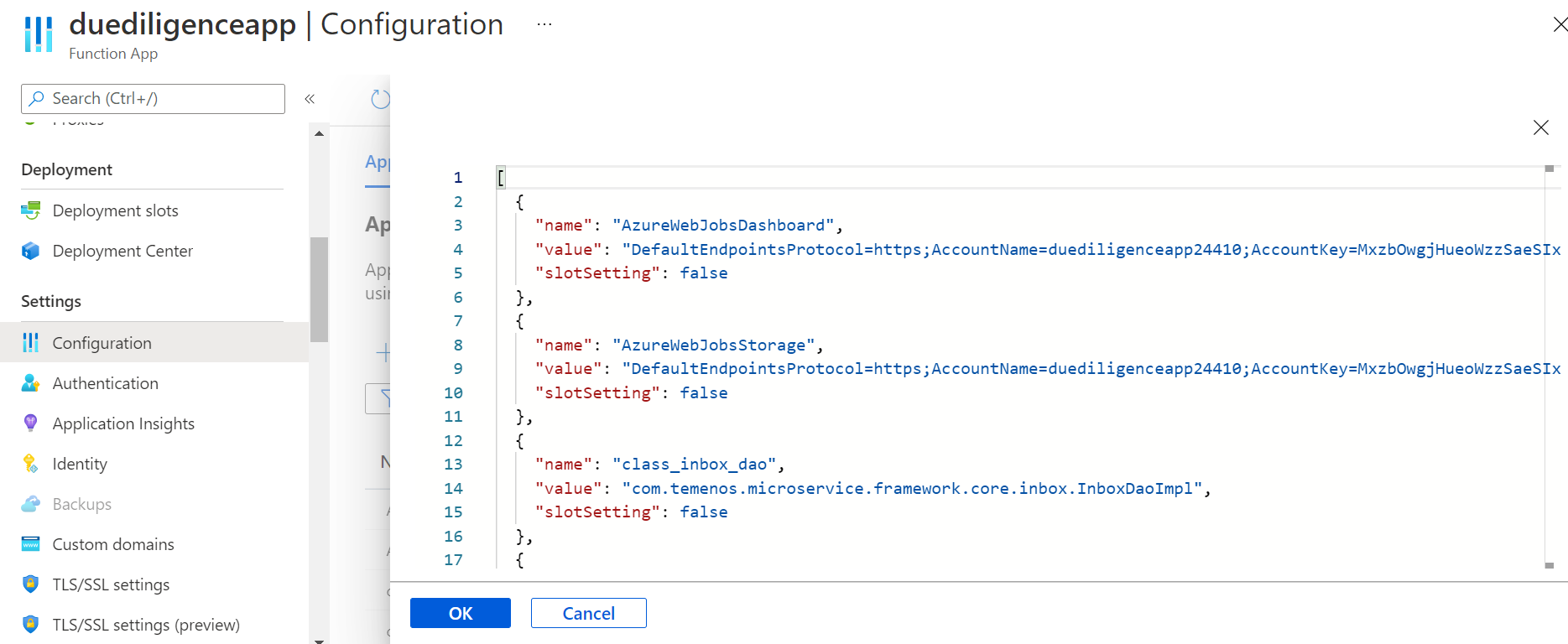
Below are the required configurations:
| PROPERTY | DEFAULT VALUE | PROPERTY | DEFAULT VALUE |
|---|---|---|---|
| RESOURCE_GROUP_NAME | duediligence-ms |
Env specific resource name can be appended. Groups all the function app and configuration of the deployment |
Resource Group Name
|
| APP_NAME | duediligenceapp |
Env specific app name can be appended. Function app for api created in azure, if App name is changed, then rename the folder in this path: ms-duediligence-package-azure-<version>\ms-duediligence-azure\target\azure-functions |
Function App
|
| LOCATION | uksouth |
location of azure account
|
Location of Azure account
|
| DISABLE_INBOX | true |
Enable or disable inbox outbox.
|
tem_msf_disableInbox
|
| Security Related Properties | |||
| AUTHZ_ENABLED | false |
Enable/Disable the XACML policy authorization. XACML policy authorization is used to configure security policies and access rights to information for APIs. |
temn_msf_security_authz_enabled
|
| PDP_CONFIG_FILE | classpath:xacml/pdp-config.xml |
Mapping the PDP-callback configuration file available in the classpath. XAML Config file path needs to be set in the property |
PDP_CONFIG
|
| PDP_RESOURCE_TYPE | API |
The value that is set in the XAML config file needs to be provided. Resource type is used to identify the policy set in the XAML config. |
temn_msf_pdp_resource_type
|
| PDP_RESOURCE_MANAGER | DUEDILIGENCE |
The value that is set in the XAML config file needs to be provided. Resource Manager is used to identify the policy set in the XAML config. |
temn_msf_pdp_resource_manager
|
| temn_entitlement_service_enabled | "false" |
Enable/Disable the entitlement service. If the property is enabled, the roles and permissions needed for the authentication will be taken from the entitlement Microservices. |
temn_entitlement_service_enabled
|
| MS_SECURITY_TOEKN_CHECK_ENABLED | N |
Enable/Disable the JWT validation. By default, JWT token check is enabled. JWT validation is used to validate the custom and mandatory claims from the provided token. |
ms_security_tokencheck_enabled
|
| ID_TOKEN_SIGNED | "true" | Signed token used for fabric | ID_TOKEN_SIGNED |
| JWT_TOKEN_ISSUER | Fabric | Identifies the issuer of the authentication token. | JWT_TOKEN_ISSUER |
| JWT_TOKEN_PRINCIPAL_CLAIM | sub | Indicates the claim in which the user principal is provided. | JWT_TOKEN_PRINCIPAL_CLAIM |
| JWT_TOKEN_PUBLIC_KEY | <JWT Token Value> | Indicates Base64 encoded public key content that can be directly loaded as a public key certificate. | JWT_TOKEN_PUBLIC_KEY |
| MongoDB Configurations | |||
| DATABASE_KEY | mongodb | name of the database key | |
| MONGODB_DBNAME | ms_duediligence | name of the database | |
| MONGODB_CONNECTIONSTR | mongodb://Temenos1:Temenos123@cluster0-shard-00-00.ojwsl.azure.mongodb.net:27017,cluster0-shard-00-01.ojwsl.azure.mongodb.net:27017,cluster0-shard-00-02.ojwsl.azure.mongodb.net:27017/ms_duediligence?ssl=true&replicaSet=atlas-m2f7lu-shard-0&authSource=admin&retryWrites=true&w=majority | URL to connect to the mongodb instance | |
| PostgresDB Configurations | |||
| DATABASE_KEY | postgresql | name of the database key | |
| POSTGRESQL_USERNAME | myadmin@duediligence | Username | |
| POSTGRESQL_CONNECTIONURL | jdbc:postgresql://duediligence.postgres.database.azure.com:5432/duediligence | URL to connect to the postgreSQLdb instance | |
| POSTGRESQL_PASSWORD | Passw0rd! | Password | |
| Common Configurations | |||
| temn.msf.security.authz.enabled | false |
Enable/Disable the XACML policy authorization.
XACML policy authorization is used to configure security policies and access rights to information for APIs. |
|
| temn_msf_name | ms-duediligence | ||
| class.package.name | com.temenos.microservice.duediligence.function | ||
| class.outbox.dao | com.temenos.microservice.framework.core.outbox.OutboxDaoImpl | ||
| class.inbox.dao | com.temenos.microservice.framework.core.inbox.InboxDaoImpl | ||
| temn.msf.ingest.is.avro.event.ingester | false | ||
| temn.msf.ingest.generic.ingester | com.temenos.microservice.framework.core.ingester.GenericCommandSTBinaryIngester | ||
| eventHubConsumerGroup | \$Default | Kafka Consumer Group | |
| temn_msf_logger_root_level | ERROR | Specifies the configuration parameter for logging.Possible Values : DEBUG,INFO,ERROR | |
| temn.msf.stream.kafka.sasl.enabled | true | To enable ssl connectivity in Kafka | |
| temn.msf.stream.kafka.sasl.jaas.config | {org.apache.kafka.common.security.plain.PlainLoginModule required username=\"\$ConnectionString\" password=\"${eventHubConnection}\";} | Property to stream or read the data from Event Hub Kafka | |
| temn.msf.stream.security.kafka.security.protocol | SASL_SSL | ||
| temn.msf.stream.kafka.sasl.mechanism | PLAIN | ||
| SCALE_CONTROLLER_LOGGING_ENABLED | AppInsights:Verbose | ||
| APPLICATIONINSIGHTS_SAMPLING_PERCENTAGE | 100 | ||
|
Below mentioned InboxOutbox and Ingester Configurations are related to GDPR.
|
|||
| InboxOutbox Configurations | |||
| EXECUTION_ENV | serverless | ||
| eventHubName | %MSF_NAME%-outbox | ||
| temn.msf.ingest.source.stream | %MSF_NAME%-outbox | ||
| temn.exec.env | serverless | ||
| temn.queue.impl | kafka | ||
| temn.msf.stream.kafka.bootstrap.servers | %EVENT_HUB_NAME_SPACE:"=%.servicebus.windows.net:9093 | ||
| temn.msf.stream.vendor.outbox | kafka | ||
| temn.msf.ingest.consumer.max.poll.records | 20 | ||
| temn.msf.ingest.is.cloud.event | true | ||
| temn_msf_stream_outbox_topic | %MSF_NAME%-outbox | ||
| temn.msf.disable.outbox.cleanup | true | ||
| temn_msf_stream_kafka_sasl_enabled | true | To enable ssl connectivity in Kafka. | |
| temn.msf.stream.vendor | kafka | ||
| tmn_inbox_source_namespace | %MSF_NAME%-inbox | ||
| tmn_outbox_source_namespace | %MSF_NAME%-outbox | ||
| Ingester Configurations | |||
| temn.msf.service.name | CommandIngester | ||
| temn.msf.exec.env | serverless | ||
| temn.msf.ingest.source.stream | %MSF_NAME%-inbox-topic | ||
| temn.msf.ingest.source.stream.consumergroup.id | %MSF_NAME%-ingester-consumer | ||
| temn.msf.ingest.sink.error.stream | %MSF_NAME%-inbox-error-topic | ||
| temn.msf.ingest.sink.error.stream.producer.id | %MSF_NAME%-ingester-error-producer | ||
| temn.msf.stream.outbox.topic | %MSF_NAME%-outbox | ||
| temn.msf.raise.commandprocessed.event.enabled | true | ||
| temn.msf.ingest.outbox.cache.namespace | ms-duediligence-outbox | ||
| tmn.ignite.host | cache-service | ||
| tmn.ignite.port | 10800 | ||
| temn.msf.ingest.inbox.cache.namespace | ms-duediligence-inbox | ||
| temn.msf.raise.received.event | true | ||
| eventHubName | %MSF_NAME%-inbox-topic | ||
| temn_msf_stream_vendor | kafka | ||
| MIN_POOL_SIZE | 10 | Specifies minimum number of connections maintained in the pool. | |
| MAX_POOL_SIZE | 150 | Specifies maximum number of connections maintained in the pool. | |
| temn_msf_outbox_stream_vendor | kafka | ||
In this topic